2018 latest Microsoft MCSA 70-417 dumps exam questions and answers free download from leads4pass. The best useful Microsoft MCSA 70-417 dumps pdf files and vce youtube demo update free shared. “Upgrading Your Skills to MCSA Windows Server 2012” is the name of Microsoft MCSA https://www.leads4pass.com/70-417.html exam dumps which covers all the knowledge points of the real Microsoft exam. High quality Microsoft MCSA 70-417 dumps pdf training materials and study guides update free try, pass Microsoft 70-417 exam test easily.
Latest Microsoft 70-417 dumps pdf files free download: https://drive.google.com/open?id=0B_7qiYkH83VRZ3pDZ1FsYVZza2M
Latest Microsoft 70-414 dumps pdf files free download: https://drive.google.com/open?id=0B_7qiYkH83VRYWNLN3FRV3d5NW8

QUESTION 1
You have a server named Server1 that runs Windows Server 2012 R2. You install the File and Storage Services server role on Server1.
From Windows Explorer, you view the properties of a folder named Folder1 and you discover that the Classification tab is missing.
You need to ensure that you can assign classifications to Folder1 from Windows Explorer manually.
What should you do?
A. Install the File Server Resource Manager role service.
B. From Folder Options, clear Hide protected operating system files (Recommended).
C. Install the Share and Storage Management Tools.
D. From Folder Options, select the Always show menus.
Correct Answer: A
Explanation:
B. Classification Management is a feature of FSRM
QUESTION 2
Your network contains an Active Directory domain named adatum.com. All domain controllers run Windows Server 2008 R2.
The domain contains a file server named Server6 that runs Windows Server 2012 R2. Server6 contains a folder named Folder1. Folder1 is shared as Share1. The NTFS permissions on Folder1 are shown in the exhibit. (Click the Exhibit button.)
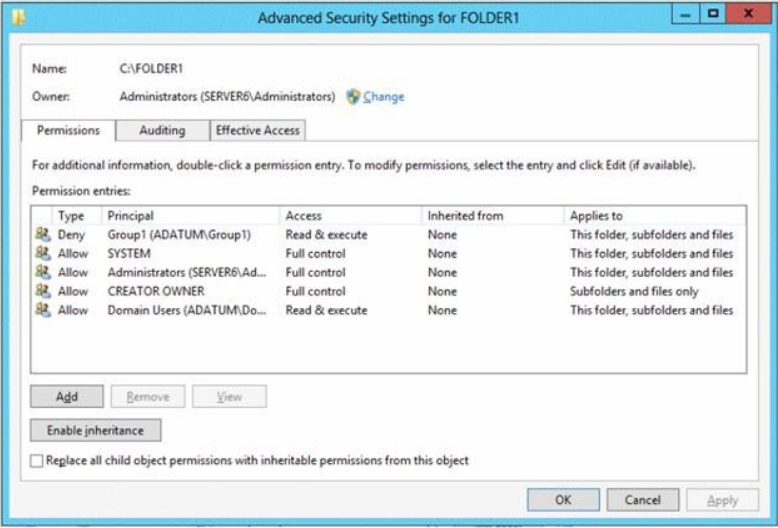
The domain contains two global groups named Group1 and Group2.
You need to ensure that only users who are members of both Group1 and Group2 are denied access to Folder1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Remove the Deny permission for Group1 from Folder1.
B. Deny Group2 permission to Folder1.
C. Install a domain controller that runs Windows Server 2012 R2.
D. Create a conditional expression.
E. Deny Group2 permission to Share1.
F. Deny Group1 permission to Share1.
Correct Answer: AD
Explanation:
* Conditional Expressions for Permission Entries Windows Server 2008 R2 and Windows 7 enhanced Windows security descriptors by introducing a conditional access permission entry. Windows Server 2012 R2 takes advantage of conditional access permission entries by inserting user claims, device claims, and resource properties, into conditional expressions. Windows Server 2012 R2 security evaluates these expressions and allows or denies access based on results of the evaluation. Securing access to resources through claims is known as claims-based access control. Claims-based access control works with traditional access control to provide an additional layer of authorization that is flexible to the varying needs of the enterprise environment.
QUESTION 3
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1 and a domain controller named DC1. All servers run Windows Server 2012 R2. 70-417 dumps
A Group Policy object (GPO) named GPO1 is linked to the domain.
Server1 contains a folder named Folder1. Folder1 is shared as Share1.
You need to ensure that authenticated users can request assistance when they are denied access to the resources on Server1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Enable the Enable access-denied assistance on client for all file types policy setting for GPO1.
B. Configure the Customize message for Access Denied errors policy setting of GPO1.
C. Install the File Server Resource Manager role service on DC1.
D. Install the File Server Resource Manager role service on Server1.
E. Assign the Read Attributes NTFS permission on Folder1 to the Authenticated Users group.
Correct Answer: AD
Explanation:
* To configure access-denied assistance by using Group Policy Open Group Policy Management. In Server Manager, click Tools, and then click Group Policy Management.
Right-click the appropriate Group Policy, and then click Edit. Click Computer Configuration, click Policies, click Administrative Templates, click System, and then click Access-Denied Assistance.
Right-click Customize message for Access Denied errors, and then click Edit.
Select the Enabled option.
Etc
*You can configure access-denied assistance within a domain by using Group Policy, or you can configure the assistance individually on each file server by using the File Server Resource Manager console.
Reference: Deploy Access-Denied Assistance
QUESTION 4
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1. The File Server Resource Manager role service is installed on Server1. All servers run Windows Server 2012 R2.
A Group Policy object (GPO) named GPO1 is linked to the organizational unit (OU) that contains Server1.
The following graphic shows the configured settings in GPO1.
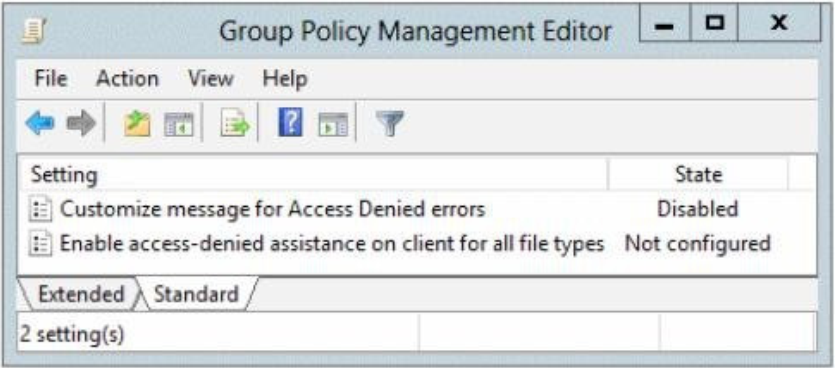
Server1 contains a folder named Folder1. Folder1 is shared as Share1.
You attempt to configure access-denied assistance on Server1, but the Enable access-denied assistance option cannot be selected from File Server Resource Manager.
You need to ensure that you can configure access-denied assistance on Server1 manually by using File Server Resource Manager.
What should you do?
A. Set the Customize message for Access Denied errors policy setting to Enabled for GPO1.
B. Set the Enable access-denied assistance on client for all file types policy setting to Disabled for GPO1.
C. Set the Enable access-denied assistance on client for all file types policy setting to Enabled for GPO1.
D. Set the Customize message for Access Denied errors policy setting to Not Configured for GPO1.
Correct Answer: D
Explanation:
Ensure that you can configure access-denied assistance .
QUESTION 5
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2.
You are creating a central access rule named Test Finance that will be used to audit members of the Authenticated users group for access failure to shared folders in the finance department.
You need to ensure that access requests are unaffected when the rule is published.
What should you do?
A. Set the Permissions to Use the following permissions as proposed permissions.
B. Add a Resource condition to the current permissions entry for the Authenticated Users principal.
C. Set the Permissions to Use following permissions as current permissions.
D. Add a User condition to the current permissions entry for the Authenticated Users principal.
Correct Answer: A
Explanation:
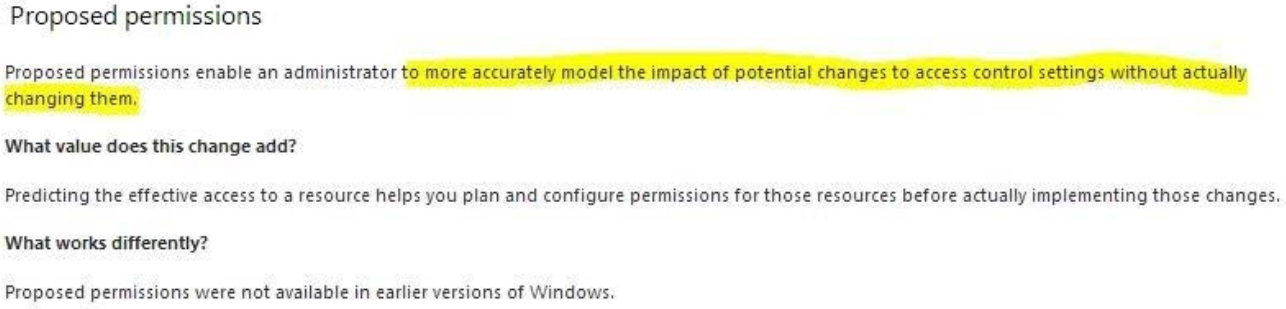
QUESTION 6
You deploy an Active Directory Federation Services (AD FS) 2.1 infrastructure. The infrastructure uses Active Directory as the attribute store.
Some users report that they fail to authenticate to the AD FS infrastructure.
You discover that only users who run third-party web browsers experience issues.
You need to ensure that all of the users can authenticate to the AD FS infrastructure successfully.
Which Windows PowerShell command should you run?
A. Set-ADFSProperties -SSOLifetime 1:00:00
B. Set-ADFSProperties -AddProxyAuthenticationRules None
C. Set-ADFSProperties -ExtendedProtectionTokenCheck None
D. Set-ADFSProperties -ProxyTrustTokenLifetime 1:00:00
Correct Answer: C
Explanation:
Disable the Extended Protection for Authentication feature in AD FS 2.0 Certain client browser software, such as Firefox, Chrome, and Safari, do not support the Extended Protection for Authentication capabilities that can be used across the Windows platform to protect against man-in-the-middle attacks. 70-417 dumps To prevent this type of attack from occurring over secure AD FS communications, AD FS 2.0 enforces (by default) that all communications use a channel binding token (CBT) to mitigate against this threat. However, if it is important that browser clients that do not support Extended Protection for Authentication must be used in your organization, you will have to adjust a feature setting in AD FS 2.0 that will disable the CBT from being used over communications, which, in turn, may leave client credentials vulnerable to man-in-themiddle attacks. If this is the case, you can disable the Extended Protection for Authentication feature by using the Windows PowerShell cmdlet Set-ADFSProperties in the following procedure.
To disable the Extended Protection for Authentication feature in AD FS 2.0 On a federation server, login using the Administrator account, open the Windows PowerShell command prompt, and then type the following command:
Set-ADFSProperties ExtendedProtectionTokenCheck None Repeat this step on each federation server in the farm.
QUESTION 7
Your network contains a perimeter network and an internal network. The internal network contains an Active Directory Federation Services (AD FS) 2.1 infrastructure. The infrastructure uses Active Directory as the attribute store.
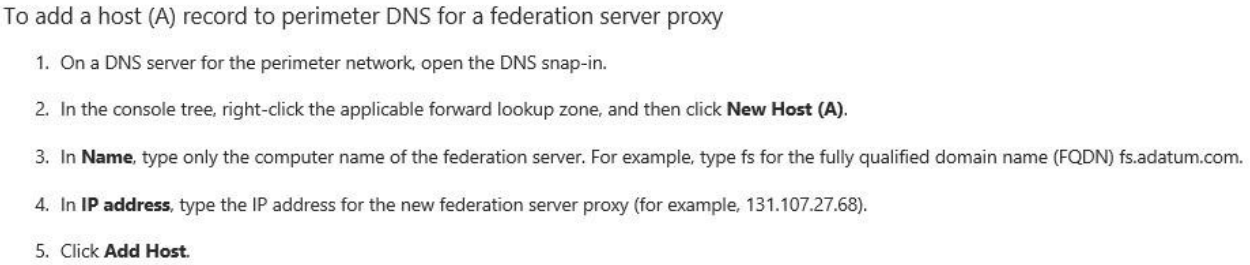
You plan to deploy a federation server proxy to a server named Server2 in the perimeter network.
You need to identify which value must be included in the certificate that is deployed to Server2.
What should you identify?
A. The name of the Federation Service
B. The name of the Active Directory domain
C. The FQDN of the AD FS server
D. The public IP address of Server2
Correct Answer: C
Explanation:
A. It must contain the FQDN
QUESTION 8
Your network contains an Active Directory domain named contoso.com. The domain contains servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 has the Active Directory Federation Services server role installed.Server2 is a file server. Your company introduces a Bring Your Own Device (BYOD) policy.
You need to ensure that users can use a personal device to access domain resources by using Single Sign-On (SSO) while they are connected to the internal network.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Enable the Device Registration Service in Active Directory.
B. Publish the Device Registration Service by using a Web Application Proxy.
C. Configure Active Directory Federation Services (AD FS) for the Device Registration Service.
D. Install the Work Folders role service on Server2.
E. Create and configure a sync share on Server2.
Correct Answer: AC
Explanation:
*Prepare your Active Directory forest to support devices This is a one-time operation that you must run to prepare your Active Directory forest to support devices.
To prepare the Active Directory forest
On your federation server, open a Windows PowerShell command window and type:
Initialize-ADDeviceRegistration
*Enable Device Registration Service on a federation server farm node To enable Device Registration Service
1.On your federation server, open a Windows PowerShell command window and type:
Enable-AdfsDeviceRegistration
2.Repeat this step on each federation farm node in your AD FS farm.
QUESTION 9
Your network contains two servers named Server1 and Server2 that run Windows Server 2008 R2.
Server1 and Server2 are nodes in a failover cluster named Cluster1. The network contains two servers named Server3 and Server4 that run Windows Server 2012 R2. Server3 and Server4 are nodes in a failover cluster named Cluster2. 70-417 dumps
You need to move all of the applications and the services from Cluster1 to Cluster2.
What should you do first from Failover Cluster Manager?
A. On a server in Cluster2, click Migrate Roles.
B. On a server in Cluster2, click Move Core Cluster Resources, and then click Select Node…
C. On a server in Cluster1, configure Cluster-Aware Updating.
D. On a server in Cluster2, click Move Core Cluster Resources, and then click Best Possible Node.
Correct Answer: A
Explanation:
QUESTION 10
Your network contains two servers named HV1 and HV2. Both servers run Windows Server 2012 R2 and have the Hyper-V server role installed.
HV1 hosts 25 virtual machines. The virtual machine configuration files and the virtual hard disks are stored in D:\VM.
You shut down all of the virtual machines on HV1.
You copy D:\VM to D:\VM on HV2.
You need to start all of the virtual machines on HV2. You want to achieve this goal by using the minimum amount of administrative effort.
What should you do?
A. From HV1, export all virtual machines to D:\VM. Copy D:\VM to D:\VM on HV2 and overwrite the existing files. On HV2, run the New Virtual Machine wizard.
B. From HV1, export all virtual machines to D:\VM. Copy D:\VM to D:\VM on HV2 and overwrite the existing files. On HV2, run the Import Virtual Machine wizard.
C. Run the Import-VM InitialReplicationcmdlet.
D. Run the Import-VM cmdlet.
Correct Answer: D
Explanation:
The Import-VM cmdlet imports a virtual machine from a file.
Newest helpful Microsoft MCSA 70-417 dumps exam practice materials in PDF format free download from leads4pass. The best and most updated latest Microsoft MCSA https://www.leads4pass.com/70-417.html dumps pdf training resources which are the best for clearing 70-417 exam test, and to get certified by Microsoft MCSA, download one of the many PDF readers that are available for free.
High quality Microsoft MCSA 70-417 dumps vce youtube: https://youtu.be/tXkM3WTTltI