2018 latest Cisco CCNP Security 300-209 dumps exam learning materials and study guides in PDF format download free try from leads4pass. “Implementing Cisco Secure Mobility Solutions” is the name of Cisco CCNP Security https://www.leads4pass.com/300-209.html exam dumps which covers all the knowledge points of the real Cisco exam.
leads4pass is the best site for providing online preparation material for 300-209 exam. Get your Cisco Implementing Cisco Secure Mobility Solutions dumps exam preparation questions in form of 300-209 SIMOS – Cisco PDF. It is the best choice for you to Cisco 300-209 exam easily in the first attempt.
Google drive Cisco 300-209 dumps pdf: https://drive.google.com/open?id=0B_7qiYkH83VROWtCY2Nqc1Yta2c
Google drive Cisco 300-206 dumps pdf: https://drive.google.com/open?id=0B_7qiYkH83VRckk2V1ZwWXl5dVk
The best 210-451 dumps training materials and youtube, latest Cisco 210-450 dumps pdf questions and answers. Download the latest useful Cisco CCNP Security 300-209 dumps vce software free try.
Best Cisco CCNP Security 300-209 Dumps Exam Questions And Answers (Q1-Q20)
QUESTION 1
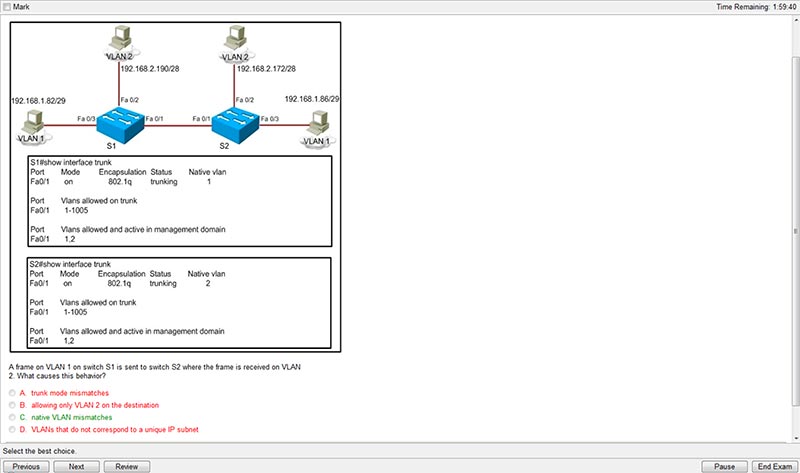
Which command will prevent a group policy from inheriting a filter ACL in a clientless SSL VPN?
A. vpn-filter none
B. no vpn-filter
C. filter value none
D. filter value ACLname
Correct Answer: C
QUESTION 2
A Cisco IOS SSL VPN gateway is configured to operate in clientless mode so that users can access file shares on a Microsoft Windows 2003 server. Which protocol is used between the Cisco IOS router and the Windows server?
A. HTTPS
B. NetBIOS
C. CIFS
D. HTTP
Correct Answer: C
QUESTION 3
A rogue static route is installed in the routing table of a Cisco FlexVPN and is causing traffic to be blackholed. Which command should be used to identify the peer from which that route originated?
A. show crypto ikev2 sa detail
B. show crypto route
C. show crypto ikev2 client flexvpn
D. show ip route eigrp
E. show crypto isakmp sa detail
Correct Answer: B
QUESTION 4
Authorization of a clientless SSL VPN defines the actions that a user may perform within a clientless SSL VPN session. Which statement is correct concerning the SSL VPN authorization process?
A. Remote clients can be authorized by applying a dynamic access policy, which is configured on an external AAA server.
B. Remote clients can be authorized externally by applying group parameters from an external database.
C. Remote client authorization is supported by RADIUS and TACACS+ protocols.
D. To configure external authorization, you must configure the Cisco ASA for cut-through proxy.
Correct Answer: B
Explanation:
CISCO SSL VPN guide
The aaa authentication command is entered to specify an authentication list or server group under a SSL VPN context configuration. If this command is not configured and AAA is configured globally on the router, global authentication will be applied to the context configuration.
The database that is configured for remote-user authentication on the SSL VPN gateway can be a local database, or the database can be accessed through any RADIUS or TACACS+ AAA server.
We recommend that you use a separate AAA server, such as a Cisco Access Control Server (ACS). A separate AAA server provides a more robust security solution. It allows you to configure unique passwords for each remote user and accounting and logging for remote-user sessions.
QUESTION 5
Refer to the exhibit.
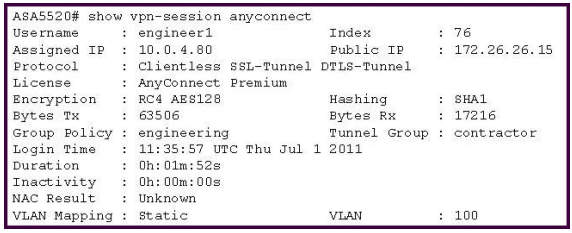
A NOC engineer needs to tune some postlogin parameters on an SSL VPN tunnel.
From the information shown, where should the engineer navigate to, in order to find all the postlogin session parameters?
A. “engineering” Group Policy
B. “contractor” Connection Profile
C. DefaultWEBVPNGroup Group Policy
D. DefaultRAGroup Group Policy
E. “engineer1” AAA/Local Users
Correct Answer: A
Explanation:
The policy group is a container that defines the presentation of the portal and the permissions for resources that are configured for a group of remote users. Entering the policy group command places the router in webvpn group policy configuration mode. After it is configured, the group policy is attached to the SSL VPN context configuration by configuring the default-group-policy command. 300-209 dumps
The following tasks are accomplished in this configuration:
The presentation of the SSL VPN portal page is configured.
A NetBIOS server list is referenced.
A port-forwarding list is referenced.
The idle and session timers are configured.
A URL list is referenced.
QUESTION 6
Which equation describes an elliptic curve?
A. y3 = x3 + ax + b
B. x3 = y2 + ab + x
C. y4 = x2 + ax + b
D. y2 = x3 + ax + b
E. y2 = x2 + ax + b2
Correct Answer: D
QUESTION 7
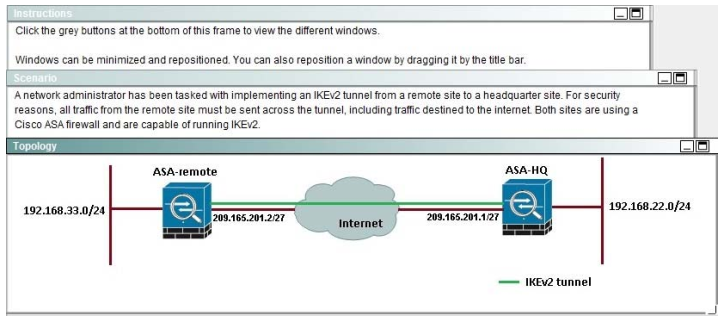
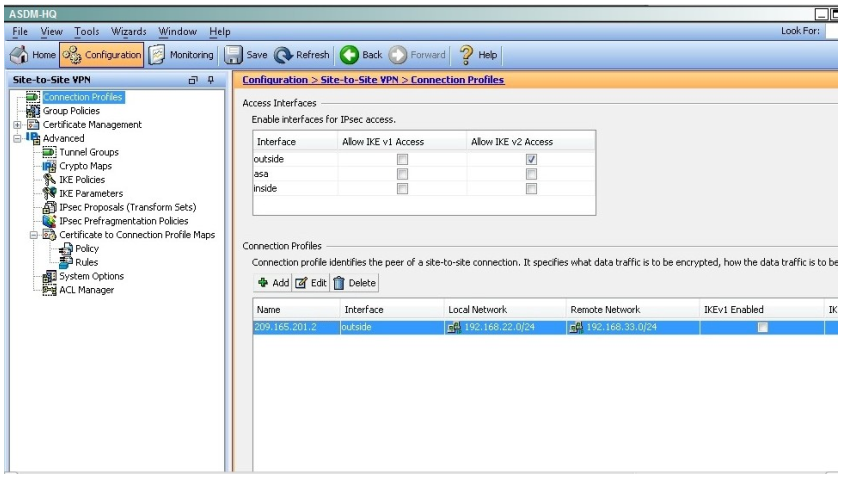
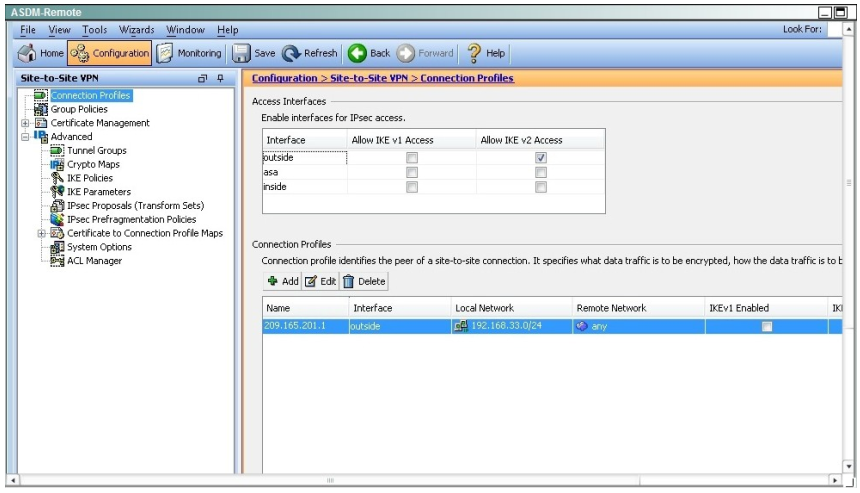
When a tunnel is initiated by the headquarter ASA, which one of the following Diffie- Hellman groups is selected by the headquarter ASA during CREATE_CHILD_SA exchange?
A. 1
B. 2
C. 5
D. 14
E. 19
Correct Answer: C
Explanation:
Traffic initiated by the HQ ASA is assigned to the static outside crypto map, which shown below to use DH group 5.
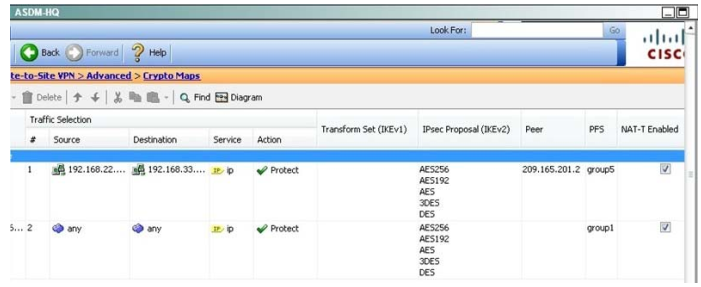
QUESTION 8
Which three changes must be made to migrate from DMVPN Phase 2 to Phase 3 when EIGRP is configured? (Choose three.)
A. Enable EIGRP next-hop-self on the hub.
B. Disable EIGRP next-hop-self on the hub.
C. Enable EIGRP split-horizon on the hub.
D. Add NHRP redirects on the hub.
E. Add NHRP shortcuts on the spoke.
F. Add NHRP shortcuts on the hub.
Correct Answer: ADE
QUESTION 9
Which cryptographic algorithms are a part of the Cisco NGE suite?
A. HIPPA DES
B. AES-CBC-128
C. RC4-128
D. AES-GCM-256
Correct Answer: D
QUESTION 10
Which Cisco ASDM option configures forwarding syslog messages to email?
A. Configuration > Device Management > Logging > E-Mail Setup
B. Configuration > Device Management > E-Mail Setup > Logging Enable
C. Select the syslogs to email, click Edit, and select the Forward Messages option.
D. Select the syslogs to email, click Settings, and specify the Destination Email Address option.
Correct Answer: A
QUESTION 11
Your corporate finance department purchased a new non-web-based TCP application tool to run on one of its servers. Certain finance employees need remote access to the software during nonbusiness hours. These employees do not have “admin” privileges to their PCs.
What is the correct way to configure the SSL VPN tunnel to allow this application to run?
A. Configure a smart tunnel for the application.
B. Configure a “finance tool” VNC bookmark on the employee clientless SSL VPN portal.
C. Configure the plug-in that best fits the application.
D. Configure the Cisco ASA appliance to download the Cisco AnyConnect SSL VPN Client to the finance employee each time an SSL VPN tunnel is established.
Correct Answer: A
Explanation:
A smart tunnel is a connection between a TCP-based application and a private site, using a clientless (browser based) SSL VPN session with the security appliance as the pathway, and the security appliance as a proxy server. You can identify applications to which you want to grant smart tunnel access, and specify the local path to each application. For applications running on Microsoft Windows, you can also require a match of the SHA-1 hash of the checksum as a condition for granting smart tunnel access.
Lotus SameTime and Microsoft Outlook Express are examples of applications to which you might want to grant smart tunnel access.
Configuring smart tunnels requires one of the following procedures, depending on whether the application is a client or is a web-enabled application:
• Create one or more smart tunnel lists of the client applications, then assign the list to the group policies or local user policies for whom you want to provide smart tunnel access.
• Create one or more bookmark list entries that specify the URLs of the web-enabled applications eligible for smart tunnel access, then assign the list to the DAPs, group policies, or local user policies for whom you want to provide smart tunnel access.
You can also list web-enabled applications for which to automate the submission of login credentials in smart tunnel connections over clientless SSL VPN sessions.
Why Smart Tunnels?
Smart tunnel access lets a client TCP-based application use a browser-based VPN connection to connect to a service. It offers the following advantages to users, compared to plug-ins and the legacy technology, port forwarding:
• Smart tunnel offers better performance than plug-ins.
• Unlike port forwarding, smart tunnel simplifies the user experience by not requiring the user connection of the local application to the local port.
• Unlike port forwarding, smart tunnel does not require users to have administrator privileges.
The advantage of a plug-in is that it does not require the client application to be installed on the remote computer.
Smart Tunnel Requirements, Restrictions, and Limitations
The following sections categorize the smart tunnel requirements and limitations.
General Requirements and Limitations
Smart tunnel has the following general requirements and limitations:
• The remote host originating the smart tunnel must be running a 32-bit version of Microsoft Windows Vista, Windows XP, or Windows 2000; or Mac OS 10.4 or 10.5.
• Smart tunnel auto sign-on supports only Microsoft Internet Explorer on Windows.
• The browser must be enabled with Java, Microsoft ActiveX, or both.
• Smart tunnel supports only proxies placed between computers running Microsoft Windows and the security appliance. Smart tunnel uses the Internet Explorer configuration (that is, the one intended for system-wide use in Windows). If the remote computer requires a proxy server to reach the security appliance, the URL of the terminating end of the connection must be in the list of URLs excluded from proxy services. If the proxy configuration specifies that traffic destined for the ASA goes through a proxy, all smart tunnel traffic goes through the proxy.
In an HTTP-based remote access scenario, sometimes a subnet does not provide user access to the VPN gateway. In this case, a proxy placed in front of the ASA to route traffic between the web and the end user’s location provides web access. However, only VPN users can configure proxies placed in front of the ASA.
When doing so, they must make sure these proxies support the CONNECT method. For proxies that require authentication, smart tunnel supports only the basic digest authentication type.
• When smart tunnel starts, the security appliance by default passes all browser traffic through the VPN session if the browser process is the same. The security appliance also does this if a tunnel-all policy applies. If the user starts another instance of the browser process, it passes all traffic through the VPN session. If the browser process is the same and the security appliance does not provide access to a URL, the user cannot open it. As a workaround, assign a tunnel policy that is not tunnel-all.
• A stateful failover does not retain smart tunnel connections. Users must reconnect following a failover.
QUESTION 12
Which two options are purposes of the key server in Cisco IOS GETVPN? (Choose two.)
A. to define group members.
B. to distribute static routing information.
C. to distribute dynamic routing information.
D. to encrypt transit traffic.
Correct Answer: AD
QUESTION 13
Which command identifies an AnyConnect profile that was uploaded to the router flash?
A. crypto vpn anyconnect profile SSL_profile flash:simos-profile.xml
B. svc import profile SSL_profile flash:simos-profile.xml
C. anyconnect profile SSL_profile flash:simos-profile.xml
D. webvpn import profile SSL_profile flash:simos-profile.xml
Correct Answer: A
QUESTION 14
A custom desktop application needs to access an internal server. An administrator is tasked with configuring the company’s SSL VPN gateway to allow remote users to work. 300-209 dumps Which two technologies would accommodate the company’s requirement? (Choose two).
A. AnyConnect client
B. Smart Tunnels
C. Email Proxy
D. Content Rewriter
E. Portal Customizations
Correct Answer: AB
QUESTION 15
Refer to the exhibit.
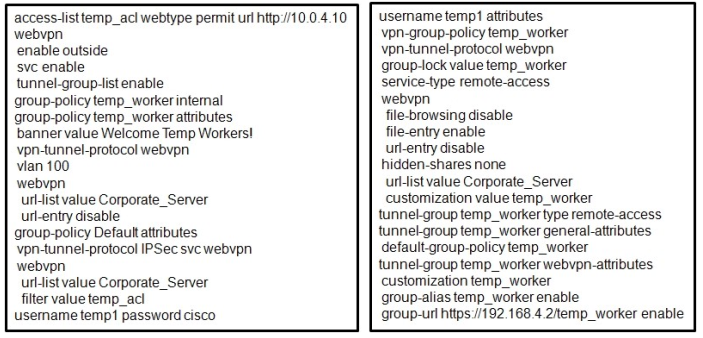
A junior network engineer configured the corporate Cisco ASA appliance to accommodate a new temporary worker. For security reasons, the IT department wants to restrict the internal network access of the new temporary worker to the corporate server, with an IP address of 10.0.4.10. After the junior network engineer finished the configuration, an IT security specialist tested the account of the temporary worker. The tester was able to access the URLs of additional secure servers from the WebVPN user account of the temporary worker.
What did the junior network engineer configure incorrectly?
A. The ACL was configured incorrectly.
B. The ACL was applied incorrectly or was not applied.
C. Network browsing was not restricted on the temporary worker group policy.
D. Network browsing was not restricted on the temporary worker user policy.
Correct Answer: B
QUESTION 16
Which three remote access VPN methods in an ASA appliance provide support for Cisco Secure Desktop? (Choose three.)
A. IKEv1
B. IKEv2
C. SSL client
D. SSL clientless
E. ESP
F. L2TP
Correct Answer: BCD
QUESTION 17
You have been using pre-shared keys for IKE authentication on your VPN. Your network has grown rapidly, and now you need to create VPNs with numerous IPsec peers. How can you enable scaling to numerous IPsec peers?
A. Migrate to external CA-based digital certificate authentication.
B. Migrate to a load-balancing server.
C. Migrate to a shared license server.
D. Migrate from IPsec to SSL VPN client extended authentication.
Correct Answer: A
QUESTION 18
Which option is a required element of Secure Device Provisioning communications?
A. the introducer
B. the certificate authority
C. the requestor
D. the registration authority
Correct Answer: A
QUESTION 19
When troubleshooting clientless SSL VPN connections, which option can be verified on the client PC?
A. address assignment
B. DHCP configuration
C. tunnel group attributes
D. host file misconfiguration
Correct Answer: C
QUESTION 20
Which VPN feature allows remote access clients to print documents to local network printers?
A. Reverse Route Injection
B. split tunneling
C. loopback addressing
D. dynamic virtual tunnels
Correct Answer: B
Google drive Cisco 300-209 dumps pdf: https://drive.google.com/open?id=0B_7qiYkH83VROWtCY2Nqc1Yta2c
Google drive Cisco 300-206 dumps pdf: https://drive.google.com/open?id=0B_7qiYkH83VRckk2V1ZwWXl5dVk
High quality Cisco CCNP Security 300-209 dumps pdf training resources which are the best for clearing 300-209 exam test, and to get certified by Cisco CCNP Security https://www.leads4pass.com/300-209.html. If you are looking to get Cisco Implementing Cisco Secure Mobility Solutions certification by passing exam 300-209 then you can pass it in one go.
New Cisco CCNP Security 300-209 dumps vce youtube: https://youtu.be/SR8PwwsGrNE