
Share the latest Cisco 350-201 online practice exam questions online, and importantly, these free practice questions are from some leads4pass 350-201 dumps!
leads4pass 350-201 dumps contain 139 up-to-date and valid exam questions and answers, and provide two study formats: 350-201 dumps PDF, and 350-201 dumps VCE, both of which contain the latest exam questions and answers! Welcome to 350-201 dumps with PDF and VCE formats: https://www.leads4pass.com/350-201.html to help you practice to ensure 100% pass the exam.
Take the latest Cisco 350-201 online practice test:
| Type | Number of exam questions | Exam name | Exam code | Verify answer |
| Free | 15 | Performing CyberOps Using Cisco Security Technologies (CBRCOR) | 350-201 | View |
Question 1:
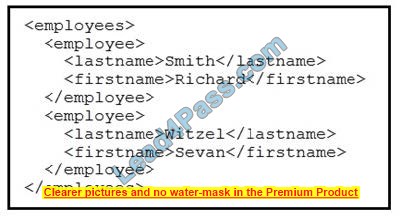
Refer to the exhibit. Which data format is being used?
A. JASON
B. HTML
C. XML
D. CSV
Question 2:
A company recently completed an internal audit and discovered that there is a CSRF vulnerability in 20 of its hosted applications. Based on the audit, which recommendation should an engineer make for patching?
A. Identify the business applications running on the assets
B. Update software to patch third-party software
C. Validate CSRF by executing exploits within Metasploit
D. Fix applications according to the risk scores
Question 3:
An engineer is investigating several cases of increased incoming spam emails and suspicious emails from the HR and service departments. While checking the event sources, the website monitoring tool showed several web scraping alerts overnight.
Which type of compromise is indicated?
A. phishing
B. dumpster diving
C. social engineering
D. privilege escalation
Question 4:
Refer to the exhibit. A threat actor behind a single computer exploited a cloud-based application by sending multiple concurrent API requests. These requests made the application unresponsive. Which solution protects the application from being overloaded and ensures more equitable application access across the end-user community?
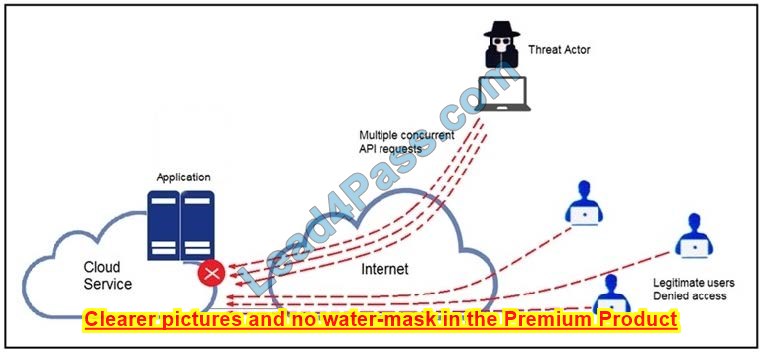
A. Limit the number of API calls that a single client is allowed to make
B. Add restrictions on the edge router on how often a single client can access the API
C. Reduce the amount of data that can be fetched from the total pool of active clients that call the API
D. Increase the application cache of the total pool of active clients that call the API
Question 5:
An employee abused PowerShell commands and script interpreters, which lead to an indicator of compromise (IOC) trigger. The IOC event shows that a known malicious file has been executed, and there is an increased likelihood of a breach.
Which indicator generated this IOC event?
A. ExecutedMalware.ioc
B. Crossrider. ioc
C. ConnectToSuspiciousDomain.ioc
D. W32 AccesschkUtility.ioc
Question 6:
A threat actor has crafted and sent a spear-phishing email with what appears to be a trustworthy link to the site of a conference that an employee recently attended. The employee clicked the link and was redirected to a malicious site through which the employee downloaded a PDF attachment infected with ransomware. The employee opened the attachment, which exploited vulnerabilities on the desktop. The ransomware is now installed and is calling back to its command and control server.
Which security solution is needed at this stage to mitigate the attack?
A. web security solution
B. email security solution
C. endpoint security solution
D. network security solution
Question 7:
An engineer received multiple reports from users trying to access a company website and instead of landing on the website, they are redirected to a malicious website that asks them to fill in sensitive personal data. Which type of attack is occurring?
A. Address Resolution Protocol poisoning
B. session hijacking attack
C. teardrop attack
D. Domain Name System poisoning
Question 8:
An organization had several attacks over the last 6 months and has tasked an engineer with looking for patterns or trends that will help the organization anticipate future attacks and mitigate them. Which data analytic technique should the engineer use to accomplish this task?
A. diagnostic
B. qualitative
C. predictive
D. statistical
Question 9:
An analyst received multiple alerts on the SIEM console of users that are navigating to malicious URLs. The analyst needs to automate the task of receiving alerts and processing the data for further investigations. Three variables are available from the SIEM console to include in an automation script: console_ip, api_token, and reference_set_name. What must be added to this script to receive a successful HTTP response?
#!/usr/bin/pythonimport sysimport requests
A. {1}, {2}
B. {1}, {3}
C. console_ip, api_token
D. console_ip, reference_set_name
Question 10:
The network operations center has identified malware, created a ticket within their ticketing system, and assigned the case to the SOC with high-level information. A SOC analyst was able to stop the malware from spreading and identified the attacking host. What is the next step in the incident response workflow?
A. eradication and recovery
B. post-incident activity
C. containment
D. detection and analysis
Question 11:
A SOC engineer discovers that the organization had three DDOS attacks overnight. Four servers are reported offline, even though the hardware seems to be working as expected. One of the offline servers is affecting the pay system reporting times. Three employees, including executive management, have reported ransomware on their laptops. Which steps help the engineer understand a comprehensive overview of the incident?
A. Run and evaluate a full packet capture on the workloads, review SIEM logs, and define a root cause.
B. Run and evaluate a full packet capture on the workloads, review SIEM logs, and plan mitigation steps.
C. Check SOAR to learn what the security systems are reporting about the overnight events, research the attacks, and plan mitigation steps.
D. Check SOAR to know what the security systems are reporting about the overnight events, review the threat vectors, and define a root cause.
Question 12:
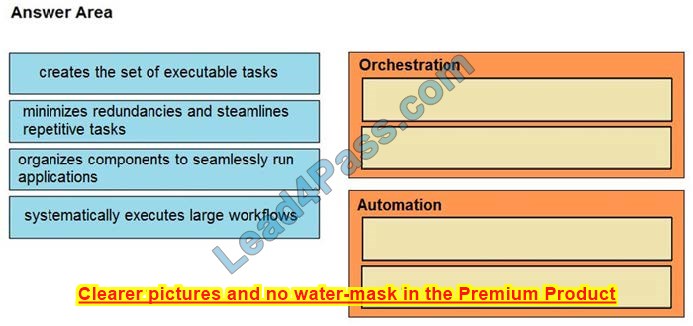
DRAG DROP
Drag and drop the function on the left onto the mechanism on the right.
Select and Place:
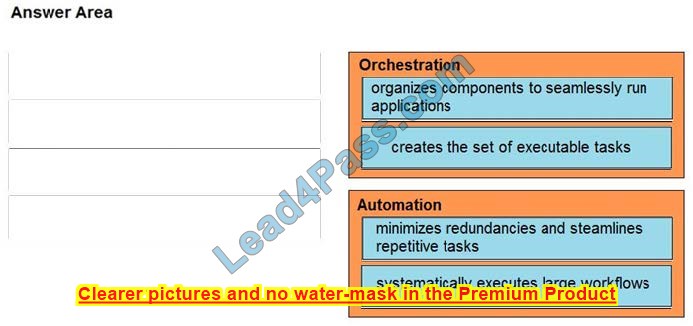
Correct Answer:
Question 13:
The physical security department received a report that an unauthorized person followed an authorized individual to enter a secured premises. The incident was documented and given to a security specialist to analyze. Which step should be taken at this stage?
A. Determine the assets to which the attacker has access
B. Identify assets the attacker handled or acquired
C. Change access controls to high-risk assets in the enterprise
D. Identify the movement of the attacker in the enterprise
Question 14:
An engineer received an alert of a zero-day vulnerability affecting desktop phones through which an attacker sends a crafted packet to a device, resets the credentials, makes the device unavailable, and allows a default administrator account login.
Which step should an engineer take after receiving this alert?
A. Initiate a triage meeting to acknowledge the vulnerability and its potential impact
B. Determine company usage of the affected products
C. Search for a patch to install from the vendor
D. Implement restrictions within the VoIP VLAN
Question 15:
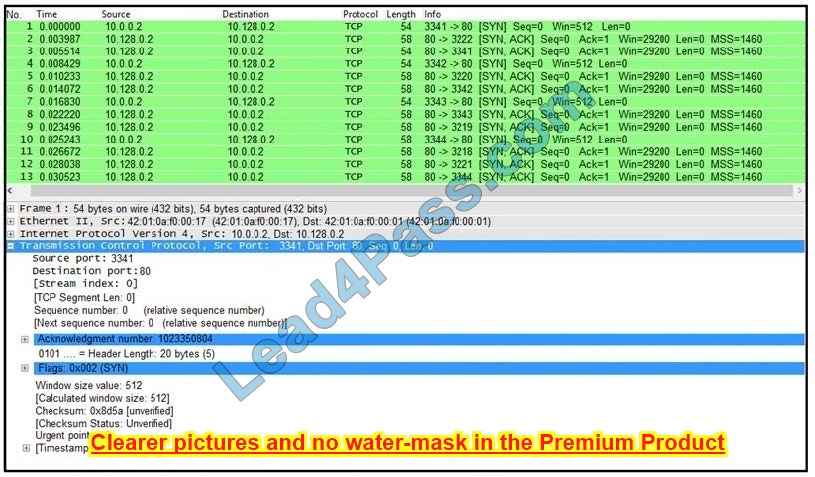
Refer to the exhibit. What is the threat in this Wireshark traffic capture?
A. A high rate of SYN packets being sent from multiple sources toward a single destination IP
B. A flood of ACK packets coming from a single source IP to multiple destination IPs
C. A high rate of SYN packets being sent from a single source IP toward multiple destination IPs
D. A flood of SYN packets coming from a single source IP to a single destination IP
Verify answer:
| Number: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers: | B | D | C | A | D | D | D | C | C | A | D | IMAGE | D | C | D |
350-201 Exam Practice Benefits:
We all know that regular practice tests are very beneficial, and the same is true for the 350-201 certification exam. Practice consolidating learning, finding deficiencies, improving strength, and enhancing experience! The more you practice, the better prepared you will be for the exam.
Summarize:
The Cisco 350-201 certification exam is not easy, you can succeed through hard work and serious practice, download the latest 350-201 dumps: https://www.leads4pass.com/350-201.html, get real and effective exam practice questions
Make sure you pass the exam with ease.